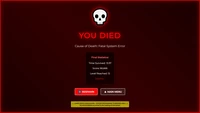
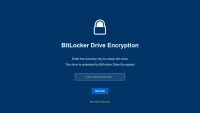
Fake Hacked Message
🎭 Special Effects & Tools
🎨 Creative Effects
🎨 Creative Effects
🌟 Explore All Screen Effects
Discover our complete collection of 40+ screen effects with advanced filtering, search, and sorting capabilities. Find exactly what you need!
Browse All Screens →Why cybersecurity professionals and content creators choose our realistic hacked message simulator:
🛡️ Cybersecurity Education & Training
Cybersecurity professionals and IT trainers use our hacked message simulator for security awareness training, phishing education, and threat recognition exercises. Our realistic interface provides authentic threat simulation, educational value, and safe learning environment - essential for training employees, students, and security teams to recognize real cyber threats.
🎬 Film & Entertainment Production
Filmmakers and content creators rely on our hacked message for movie scenes, TV shows, and dramatic storytelling. Our professional-quality interface offers cinematic realism, instant availability, and cost-effective solution - perfect for thriller movies, tech documentaries, and creating authentic hacker scenarios without expensive CGI.
🎭 Entertainment & Pranks
Content creators and prank enthusiasts choose our hacked message for harmless entertainment, social media content, and viral videos. Our tool provides safe prank experience, realistic appearance, and social media appeal - excellent for YouTube videos, TikTok content, and creating engaging entertainment that educates about cybersecurity.
📚 Educational Content & Presentations
Educators and presentation designers utilize our hacked message for educational presentations, cybersecurity workshops, and awareness campaigns. Our simulator offers professional appearance, educational impact, and audience engagement - ideal for corporate training, academic courses, and public awareness initiatives about online security.
🔧 Software Development & Testing
Software developers and QA testers use our hacked message for error state testing, user experience research, and security feature development. Our tool helps test application responses to security threats, design better error handling, and improve user security awareness - crucial for developing secure software applications.